|
This is not a reference or tutorial on Windows 2000 Group Policy.
There are whole books written for that. This document is meant
to highlight some of the more important and maybe less known information
about Group Policies. At the bottom of the page are links to more
detailed information on Group Policies.
What are Group Policies?
Group Policies are settings that can be applied to Windows computers,
users or both. In Windows 2000 there are hundreds of Group
Policy settings. Group Policies are usually used to lock down some
aspect of a PC. Whether you don't want users to run Windows
Update or change their Display Settings, or you want to insure certain
applications are installed on computers - all this can be done with
Group Policies.
Group Policies can be configured either Locally or by Domain
Polices. Local policies can be accessed by clicking Start, Run
and typing gpedit.msc. They can also be accessed by opening
the Microsoft Management Console (Start, Run type mmc), and adding
the Group Policy snap-in. You must be an Administrator to
configure/modify Group Policies. Windows 2000 Group Policies
can only be used on Windows 2000 computers or Windows XP computers.
They cannot be used on Win9x or WinNT computers.
Domain Policies are applied to computers and users who are members
of a Domain, and these policies are configured on Domain Controllers.
You can access Domain Group Polices by opening Active Directory
Sites and Services (these policies apply to the Site level only)
or Active Directory Users and Computers (these policies apply to
the Domain and/or Organizational Units).
To create a Domain Group Policy Object open Active Directory Sites
and Services and right click Default-First-Site-Name or another
Site name, choose properties, then the Group Policy tab, then click
the New button. Give the the GPO a name, then click
the Edit button to configure the policies.
For Active Directory Users and Computers, it the same process except
you right click the Domain or an OU and choose properties.
Who can Create/Modify Group Policies?
You have to have Administrative privileges to create/modify group
policies. The following table shows who can create/modify
group policies:
| Policy Type |
Allowable Groups/Users |
| Site Level Group Policies |
Enterprise Administrators and/or
Domain Administrators in the root domain. The root domain is
the first domain created in a tree or forest. The Enterprise
Administrators group is found only in the root domain. |
| Domain Level Group Policies |
Enterprise Administrators, Domain
Administrators or members of the built-in group - Group Policy
Creator Owners. By default only the Administrator user
account is a member of this group |
| OU Level Group Policies |
Enterprise Administrators, Domain
Administrators or members of the Group Policy Creator Owners.
By default only the Administrator user account is a member
of this group.
Additionally, at the OU level, users can be delegated control
for the OU Group Policies by starting the Delegate Control Wizard
(right click the OU and choose Delegate Control). However, the
wizard only allows the delegated user to Link already created
group policies to the OU. If you want to give the OU administrators
control over creating/modifying group policies, add them to
the Group Policy Creator Owners group for the domain. |
| Local Group Policies |
The local Administrator user account
or members of the local Administrators group. |
How are Group Policies Applied?
Group Polices can be configured locally, at the Site level,
the Domain level or at the Organizational Unit (OU) level. Group
Policies are applied in a Specific Order, LSDO - Local policies
first, then Site based policies, then Domain level
policies, then OU polices, then nested OU polices
(OUs within OUs). Group polices cannot be linked to a specific user
or group, only container objects.
In order to apply Group Polices to specific users or computers,
you add users (or groups) and computers to container objects. Anything
in the container object will then get the policies linked to that
container. Sites, Domains and OUs are considered container objects.
Computer and User Active Directory objects do not have to
put in the same container object. For example, Sally the user is
an object in Active Directory. Sally's Windows 2000 Pro PC is also
an object in Active Directory. Sally the user object can be in one
OU, while her computer object can be another OU. It all depends
on how you organize your Active Directory structure and what Group
Policies you want applied to what objects.
User and Computer Policies
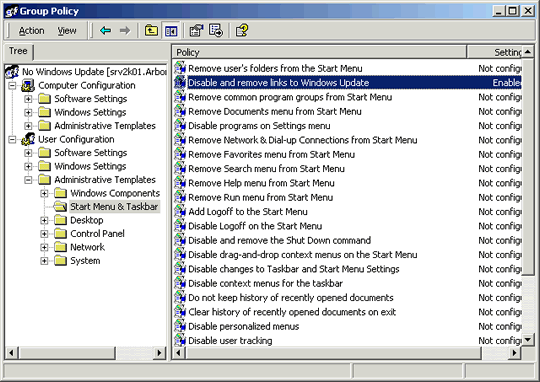
There are two nodes in each Group Policy Object that is created. A
Computer node and a User Node. They are called Computer
Configuration and User Configuration (see image above).
The polices configured in the Computer node apply to the computer
as a whole. Whoever logs onto that computer will see those policies.
Note: Computer policies are also referred to as machine policies.
User policies are user specific. They only apply to the user
that is logged on. When creating Domain Group Polices you
can disable either the Computer node or User node of the Group Policy
Object you are creating. By disabling a node that no policies
are defined for, you are decreasing the time it takes to apply the
polices.
To disable the node polices: After creating a Group Policy
Object, click that Group Policy Object on the Group Policy tab,
then click the Properties button. You will see two check boxes
at the bottom of the General tab.
It's important to understand that when Group Policies are being
applied, all the policies for a node are evaluated first,
and then applied. They are not applied one after the other.
For example, say Sally the user is a member of the Development OU,
and the Security OU. When Sally logs onto her PC the policies
set in the User node of the both the Development OU and the Security
OU Group Policy Objects are evaluated, as a whole, and then applied
to Sally the user. They are not applied Development OU first,
and then Security OU (or visa- versa).
The same goes for Computer policies. When a computer boots
up, all the Computer node polices for that computer are evaluated,
then applied.
When computers boot up, the Computer policies are applied.
When users login, the User policies are applied. When
user and computer group policies overlap, the computer policy
wins.
Note: IPSec and EFS policies are not additive. The
last policy applied is the policy the user/computer will have.
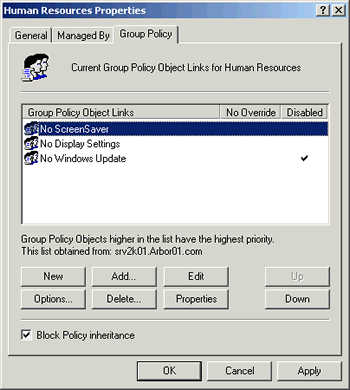
When applying multiple Group Policies Objects from any container,
Group Policies are applied from bottom to top in the Group Policy
Object list. The top Group Policy in the list is the last to be
applied. In the above image you can see three Group Policy Objects
associated with the Human Resources OU. These polices would be applied
No Windows Update first, then No Display Settings, then No ScreenSaver.
If there were any conflicts in the policy settings, the one
above it would take precedence.
Disabling Group Policy Objects
When you are creating a Group Policy Object, the changes happen
immediately. There is no "saving" of GPOs. To
prevent a partial GPO from being applied, disable the GPO
while you are configuring it. To do this, click the Group Policy
Object on the Group Policy tab and under the Disable column, double
click - a little check will appear. Click the Edit button,
make your changes, then double click under the Disable column to
re-enable the GPO. Also, if you want to temporarily disable
a GPO for troubleshooting reasons, this is the place to do it. You
can also click the Options button on the Group Policy tab and select
the Disabled check box.
Scripts
Startup scripts are processed at computer bootup and before
the user logs in.
Shutdown scripts are processed after a user logs off, but
before the computer shuts down.
Login scripts are processed when the user logs in.
Logoff scripts are processed when the user logs off, but
before the shutdown script runs.
==========================================================
Refreshing Policies
Group Policies can be applied when a computer boots up, and/or when
a user logs in. However, policies are also refreshed automatically
according to a predefined schedule. This is called Background
Refresh.
Policies not affected by background refresh. These policies are
only applied at logon time:
Folder Redirection
Software Installation
Logon, Logoff, Startup, Shutdown Scripts
Background refresh for non DCs (PCs and Member Servers)
is every 90 mins., with a +/- 30 min.
interval. So the refresh could be 60, 90 or 120 mins. For DCs
(Domain Controllers), background refresh is every 5 mins.
Also, every 16 hours every PC will request all group policies
to be reapplied (user and machine) These settings can be changed under
Computer and User Nodes, Administrative Templates,
System, Group Policy.
Using the command line to refresh policies
Secedit.exe is a command line tool that can be used to refresh
group policies on a Windows 2000 computer. To use secedit,
open a command prompt and type:
secedit /refreshpolicy user_policy to refresh
the user policies
secedit /refreshpolicy machine_policy to refresh
the machine (or computer) policies
These parameters will only refresh any user or computer policies
that have changed since the last refresh. To force a reload
of all group policies regardless of the last change, use:
secedit /refreshpolicy user_policy /enforce
secedit /refreshpolicy machine_policy /enforce
Gpupdate.exe is a command line tool that can be used to
refresh group policies on a Windows XP computer. It has replaced
the secedit command. To use gpupdate, open a command prompt
and
type:
gpupdate /target:user to refresh the user policies
gpupdate /target:machine to refresh
the machine (or computer) policies
As with secedit, these parameters will only refresh any user or
computer policies that have changed since the last refresh. To
force a reload of all group policies regardless of the last change,
use:
gpupdate /force
Notice the /force switch applies to both user and computer policies.
There is no separation of the two like there is with secedit.
==========================================================
Default Setting for Dial-up users
Win2000 considers a slow dial-up link as anything less than 500kbps.
When a user logs into a domain on a link under 500k some policies
are not applied.
Windows 2000 will automatically detect the speed of the dial-up
connection and make a decision about applying Group Policies. Some
policies are always applied regardless of the speed of the dial-up
connection. These are:
Administrative Templates
Security Settings
EFS Recovery
IPSec
Policies Not applied over slow links:
IE Maintenance Settings
Folder Redirection
Scripts
Disk Quota settings
Software Installation and Maintenance
These settings can be changed under Computer and User Nodes, Administrative
Templates,
System, Group Policy.
If the user connects to the domain using "Logon Using Dial-up
Connection" from the logon screen, once the user is authenticated,
the computer policies are applied first, followed by the user policies.
If the user connects to the domain using "Network and Dial-up
Connections", after they logon, the policies are applied
using the standard refresh cycle.
==========================================================
Default Group Policies
There are two default group policy objects that are created
when a domain is created. The Default Domain policy and the
Default Domain Controllers policy.
Default Domain Policy - this GPO can be found under the group
policy tab for that domain. It is the first policy listed.
The default domain policy is unique in that certain policies
can only be applied at the domain level.
If you double click this GPO and drill down to Computer Configuration,
Windows Settings, Security Settings, Account Policies, you will
see three policies listed:
Password Policy
Acount Lockout Policy
Kerberos Policy
These 3 policies can only be set at the domain level. If you
set these policies anywhere else- Site or OU, they are ignored.
However, setting these 3 policies at the OU level will
have the effect of setting these policies for users who log on locally
to their PCs. Login to the domain you get the domain policy,
login locally you get the OU policy.
If you drill down to Computer Configuration, Windows Settings, Security
Settings, Local Policies, Security Options, there are 3 policies
that are affected by Default Domain Policy:
Automatically log off users when logon time expires
Rename Adminsitrator Account - When set at the domain level, it
affects the Domain Administrator account only.
Rename Guest Account - When set at the domain level, it affects
the Domain Guest account only.
The Default Domain Policy should be used only for the policies listed
above. If you want to create additional domain level policies,
you should create additional domain level GPOs.
Do not delete the Default Domain Policy. You can disable it,
but it is not recommended.
Default Domain Controllers Policy - This policy can be found
by right clicking the Domain Controllers OU, choosing Properties,
then the Group Policy tab. This policy affects all Domain
Controllers in the domain regardless of where you put the domain
controllers. That is, no matter where you put your domain
controllers in Active Directory (whatever OU you put them in), they
will still process this policy.
Use the Default Domain Controllers Policy to set local policies
for your domain controllers, e.g. Audit Policies, Event Log settings,
who can logon locally and so on.
|