|
Introduction 
In a Windows 2000 domain environment, all of
the domain controllers are piers. There are no PDCs and BDCs
that you find in a Windows NT domain. All Windows 2000 domain
controllers contain a writable replica (or copy) of the Active Directory
Database, and unlike the hierarchical server structure in a Windows
NT domain (the PDC with subordinate BDCs), all domain controllers
are equal.
The ability of all domain controllers in a Windows 2000 domain to
update Active Directory, and then replicate it out to the other
DCs, is referred to as Multimaster Replication. Compare that
to a Windows NT domain which uses Single Master replication - the
PDC has the only writable copy of the SAM and all updates can only
happen at the PDC.
(The SAM, Security Accounts Database, is replaced by the Active
Directory Database in Windows 2000.)
So why are there FSMO server roles? Since each DC in a Windows
2000 domain can update the Active Directory, which then gets replicated
to all othe DCs, what happens if more than one person is making
the same change to Active Directory at the same time? There
are certain rules that are followed to prevent conflicts in updating
the AD database, but some changes are to important to the domain
to be left to these rules. Because of this, Microsoft came
up with the idea of the Flexible Single Master Operations server
roles. The servers that hold these FSMO roles are responsible
for updating certain aspects of Active Directory. By making
designated servers responsible for certain updates, instead of allowing
every server to make all updates, you prevent conflicts in Active
Directory updates.
In a Windows 2000 Domain environment, there are 5 server roles that
are necessary for the proper functioning of the forest/domain (or
Active Directory). These 5 server roles are collectively known
as the Flexible Single Master Operations Roles or FSMO roles. All
FSMO server roles exist on Domain Controllers. They do not exist
on member servers. Two of the server roles exist at the Forest
level and 3 server roles exist at the Domain level.
For example: If your Active Directory contains one forest
and 1 domain, you would have 5 FSMO role holders. If your
AD contained one forest and 2 domains, you would have 8 FSMO role
holders - two at the forest level and 3 for each domain. Likewise,
for an AD with one forest and 3 domains, you would have 11 server
roles - two at the forest level and 3 for each domain.
FSMO Roles 
The 5 FSMO server roles:
| Schema Master |
Forest Level |
One per forest |
| Domain Naming Master |
Forest Level |
One per forest |
| PDC Emulator |
Domain Level |
One per domain |
| RID Master |
Domain Level |
One per domain |
| Infrastructure Master |
Domain Level |
One per domain |
| 1. Schema Master (Forest
level) |
| The schema master FSMO role holder is the Domain Controller
responsible for performing updates to the active directory schema.
It contains the only writable copy of the AD schema. This
DC is the only one that can process updates to the directory
schema, and once the schema update is complete, it is replicated
from the schema master to all other DCs in the forest. There
is only one schema master in the forest. |
| 2. Domain Naming Master
(Forest level) |
| The domain naming master FSMO role holder is
the DC responsible for making changes to the forest-wide domain
name space of the directory. This DC is the only one that
can add or remove a domain from the directory, and that is it's
major purpose. It can also add or remove cross references
to domains in external directories. There is only one
domain naming master in the active directory or forest. |
| 3. PDC Emulator (Domain
level) |
In a Windows 2000 domain, the PDC emulator server
role performs the following functions:
 Password
changes performed by other DCs in the domain are replicated
preferentially to the PDC emulator first. Password
changes performed by other DCs in the domain are replicated
preferentially to the PDC emulator first.
 Authentication
failures that occur at a given DC in a domain because of an
incorrect password are forwarded to the PDC emulator for validation
before a bad password failure message is reported to the user. Authentication
failures that occur at a given DC in a domain because of an
incorrect password are forwarded to the PDC emulator for validation
before a bad password failure message is reported to the user.
 Account
lockout is processed on the PDC emulator. Account
lockout is processed on the PDC emulator.
 Time
synchronization for the domain. Time
synchronization for the domain.
 Group
Policy changes are preferentially written to the PDC emulator. Group
Policy changes are preferentially written to the PDC emulator.
Additionally, if your domain is a mixed mode domain that contains
Windows NT 4 BDCs, then the Windows 2000 domain controller,
that is the PDC emulator, acts as a Windows NT 4 PDC to the
BDCs.
There is only one PDC emulator per domain.
Note: Some consider the PDC emulator to only be relevant
in a mixed mode domain. This is not true. Even after you
have changed your domain to native mode (no more NT 4 domain
controllers), the PDC emulator is still necessary for the reasons
above. |
| 4. RID Master (Domain
level) |
| The RID master FSMO role holder is the single
DC responsible for processing RID Pool requests from all DCs
within a given domain. It is also responsible for removing an
object from its domain and putting it in another domain during
an object move.
When a DC creates a security principal object such as a user,
group or computer account, it attaches a unique Security ID
(SID) to the object. This SID consists of a domain SID (the
same for all SIDs created in a domain), and a relative ID
(RID) that makes the object unique in a domain.
Each Windows 2000 DC in a domain is allocated a pool of RIDs
that it assigns to the security principals it creates. When
a DC's allocated RID pool falls below a threshold, that DC
issues a request for additional RIDs to the domain's RID master.
The domain RID master responds to the request by retrieving
RIDs from the domain's unallocated RID pool and assigns them
to the pool of the requesting DC.
There is one RID master per domain in a directory.
|
| 5. Infrastructure Master
(Domain level) |
The DC that holds the Infrastructure Master FSMO
role is responsible for cross domain updates and lookups. When
an object in one domain is referenced by another object in another
domain, it represents the reference by the GUID, the SID (for
references to security principals), and the distinguished name
(DN) of the object being referenced. The Infrastructure role
holder is the DC responsible for updating an object's SID and
distinguished name in a cross-domain object reference.
When a user in DomainA is added to a group in DomainB, then
the Infrastructure master is involved. Likewise, if that
user in DomainA, who has been added to a group in DomainB, then
changes his username in DomainA, the Infrastructure master must
update the group membership(s) in DomainB with the name change.
There is only one Infrastructure master per domain. |
| |
What if a FSMO server fails? 
| Schema Master |
No updates to the Active Directory schema will
be possible. Since schema updates are rare (usually done by
certain applications and possibly an Administrator adding an
attribute to an object), then the malfunction of the server
holding the Schema Master role will not pose a critical problem. |
| Domain Naming Master |
The Domain Naming Master must be available when
adding or removing a domain from the forest (i.e. running DCPROMO).
If it is not, then the domain cannot be added or removed. It
is also needed when promoting or demoting a server to/from a
Domain Controller. Like the Schema Master, this functionality
is only used on occasion and is not critical unless you are
modifying your domain or forest structure. |
| PDC Emulator |
The server holding the PDC emulator role will
cause the most problems if it is unavailable. This would
be most noticeable in a mixed mode domain where you are still
running NT 4 BDCs and if you are using downlevel clients (NT
and Win9x). Since the PDC emulator acts as a NT 4 PDC, then
any actions that depend on the PDC would be affected (User Manager
for Domains, Server Manager, changing passwords, browsing and
BDC replication).
In a native mode domain the failure of the PDC emulator isn't
as critical because other domain controllers can assume most
of the responsibilities of the PDC emulator. |
| RID Master |
The RID Master provides RIDs for security principles
(users, groups, computer accounts). The failure of this FSMO
server would have little impact unless you are adding a very
large number of users or groups.
Each DC in the domain has a pool of RIDs already, and a problem
would occur only if the DC you adding the users/groups on ran
out of RIDs. |
| Infrastructure Master |
This FSMO server is only relevant in a multi-domain
environment. If you only have one domain, then the Infrastructure
Master is irrelevant. Failure of this server in a multi-domain
environment would be a problem if you are trying to add objects
from one domain to another. |
Placing FSMO Server Roles 
So where are these FSMO server roles found? Is there a one to
one relationship between the server roles and the number of servers
that house them?
The first domain controller that is installed in a Windows 2000 domain,
by default, holds all five of the FSMO server roles. Then, as
more domain controllers are added to the domain, the FSMO roles can
be moved to other domain controllers. Moving a FSMO server role
is a manual process, it does not happen automatically. But what
if you only have one domain controller in your domain? That
is fine. If you have only one domain controller in your organization
then you have one forest, one domain, and of course the one domain
controller. All 5 FSMO server roles will exist on that DC. There
is no rule that says you have to have one server for each FSMO server
role.
However, it is always a good idea to have more than one domain controller
in a domain for a number of reasons. Assuming you do have multiple
domain controllers in your domain, there are some best practices to
follow for placing FSMO server roles.
 The Schema Master and Domain Naming Master should reside on the
same server, and that machine should be a Global Catalog server.
Since all three are, by default, on the first domain
controller installed in a forest, then you can leave them as they
are.
The Schema Master and Domain Naming Master should reside on the
same server, and that machine should be a Global Catalog server.
Since all three are, by default, on the first domain
controller installed in a forest, then you can leave them as they
are.
Note: According to MS, the Domain Naming master needs to
be on a Global Catalog Server. If you are going to separate
the Domain Naming master and Schema master, just make sure they
are both on Global Catalog servers.
 The Infratructure
Master should not be on the same server that acts as a Global Catalog
server. The Infratructure
Master should not be on the same server that acts as a Global Catalog
server.
The reason for this is the Global Catalog contains information about
every object in the forest. When the Infrastructure Master, which
is responsible for updating Active Directory information about cross
domain object changes, needs information about objects not in it's
domain, it contacts the Global Catalog server for this information.
If they both reside on the same server, then the Infratructure
Master will never think there are changes to objects that reside
in other domains because the Global Catalog will keep it contantly
updated. This would result in the Infrastructure Master never
replicating changes to other domain controllers in it's domain.
Note: In a single domain environment this is not an issue.
 Microsoft
also recommeds that the PDC Emulator and RID Master be on the same
server. This is not mandatory like the Infrastructure Master
and the Global Catalog server above, but is recommended. Also, since
the PDC Emulator will receive more traffic than any other FSMO role
holder, it should be on a server that can handle the load. Microsoft
also recommeds that the PDC Emulator and RID Master be on the same
server. This is not mandatory like the Infrastructure Master
and the Global Catalog server above, but is recommended. Also, since
the PDC Emulator will receive more traffic than any other FSMO role
holder, it should be on a server that can handle the load.
 It is also
recommended that all FSMO role holders be direct replication partners
and they have high bandwidth connections to one another as well
as a Global Catalog server. It is also
recommended that all FSMO role holders be direct replication partners
and they have high bandwidth connections to one another as well
as a Global Catalog server.
FSMO Tools 
How do find out what servers in your domain/forest hold what server
roles? How do you move a server role from one server to another?
There are several tools that can be used to find out this
information.
Permissions
Before you can transfer a role, you must have the appropriate permissions
depending on which role you plan to transfer:
| Schema Master |
member of the Schema Admins group |
| Domain Naming Master |
member of the Enterprise Admins group |
| PDC Emulator |
member of the Domain Admins group and/or the Enterprise
Admins group |
| RID Master |
member of the Domain Admins group and/or the Enterprise
Admins group |
| Infrastructure Master |
member of the Domain Admins group and/or the Enterprise
Admins group |
Active Directory Users and Computers - use this snap-in to
find out where the domain level FSMO roles are located (PDC Emulator,
RID Master, Infrastructure Master), and also to change the location
of one or more of these 3 FSMO roles.
Open Active Directory Users and Computers, right click on the domain
you want to view the FSMO roles for and click "Operations Masters".
A dialog box (below) will open with three tabs, one for each
FSMO role. Click each tab to see what server that role resides
on. To change the server roles, you must first connect
to the domain controller you want to move it to. Do this by
right clicking "Active Directory Users and Computers"
at the top of the Active Directory Users and Computers snap-in and
choose "Connect to Domain Controller". Once connected
to the DC, go back into the Operations Masters dialog box, choose
a role to move and click the Change button.
When you do connect to another DC, you will notice the name of that
DC will be in the field below the Change button (not in this graphic).

Active Directory Domains and Trusts - use this snap-in to
find out where the Domain Naming Master FSMO role is and to change
it's location.
The process is the same as it is when viewing and changing the Domain
level FSMO roles in Active Directory Users and Computers, except
you use the Active Directory Domains and Trusts snap-in. Open Active
Directory Domains and Trusts, right click "Active Directory
Domains and Trusts" at the top of the tree, and choose "Operations
Master". When you do, you will see the dialog box below.
Changing the server that houses the Domain Naming Master
requires that you first connect to the new domain controller, then
click the Change button. You can connect to another domain
controller by right clicking "Active Directory Domains and
Trusts" at the top of the Active Directory Domains and Trusts
snap-in and choosing "Connect to Domain Controller".

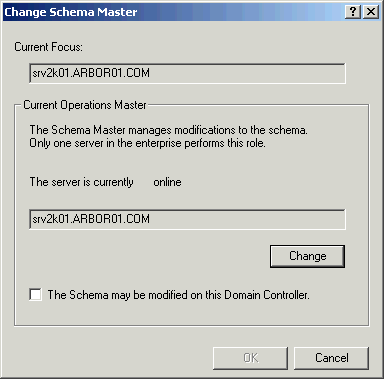
Active Directory Schema - this snap-in is used to view and
change the Schema Master FSMO role. However... the Active Directory
Schema snap-in is not part of the default Windows 2000 administrative
tools or installation. You first have to install the Support
Tools from the \Support directory on the Windows 2000 server CD
or install the Windows 2000 Server Resource Kit. Once you
install the support tools you can open up a blank Microsoft Management
Console (start, run, mmc) and add the snap-in to the console. Once
the snap-in is open, right click "Active Directory Schema"
at the top of the tree and choose "Operations Masters".
You will see the dialog box below. Changing the server
the Schema Master resides on requires you first connect to another
domain controller, and then click the Change button.
You can connect to another domain controller by right clicking "Active
Directory Schema" at the top of the Active Directory Schema
snap-in and choosing "Connect to Domain Controller".
More Tools
In addition to the tools mentioned above, there are other tools
that can be used to view the FSMO server roles. Perhaps the
easiest and fastest way to find out what server holds what FSMO
role is by using the Netdom command line utility. Like
the Active Directory Schema snap-in, the Netdom utility is only
available if you have installed the Support Tools from the Windows
2000 CD or the Win2K Server Resource Kit.
To use Netdom to view the FSMO role holders, open a command prompt
window and type:
netdom query fsmo and press enter. You will see a list of
the FSMO role servers:

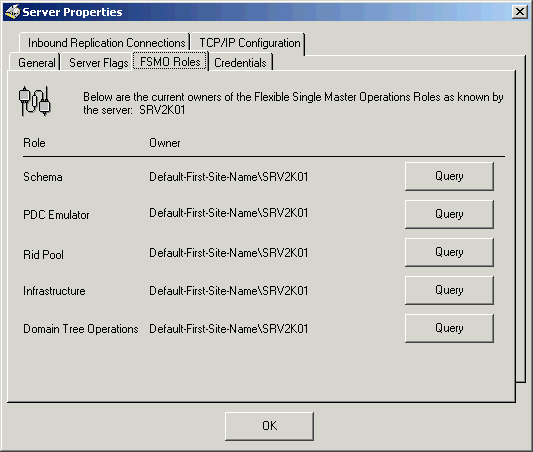
Another tool that comes with the Support Tools is the Active
Directory Relication Monitor. Open this utility from Start,
Programs, Windows 2000 Support Tools. Once open, click Edit,
Add Monitored Server and add the name of a Domain Controller. Once
added, right click the Server name and choose properties. Click
the FSMO Roles tab to view the servers holding the 5 FSMO roles
(below). You cannot change roles using Replication Monitor, but
this tool has many other useful purposes in regard to Active Directory
information. It is something you should check out if you haven't
already.
Finally, you can use the Ntdsutil.exe utility to gather information
about and change servers for FSMO roles. Ntdsutil.exe, a command
line utility that is installed with Windows 2000 server, is rather
complicated and beyond the scope of this document.
Links 
Transferring and Seizing a FSMO Role
http://support.microsoft.com/default.aspx?scid=kb;en-us;Q255504
Placement of FSMO role holders
http://support.microsoft.com/default.aspx?scid=kb;en-us;Q223346
Download Adcheck
(470k). A simple utility to view information about AD and
FSMO roles.
Active
Directory Design and Deployment by Gary L. Olsen. Excellent
book about Active Directory.
|